The MPEG-1 standard was an offspring of its age. Just as CD Audio had no content protection provision – something the music industry had come to regret – the MPEG-1 standard has no content protection provision.
MPEG-2 is a different story. Even without considering subscription-based CATV, pay TV, both on terrestrial and satellite networks, was not unknown in the early 1990s. Most of the pay TV available at that time was good old composite television with some tricks to scramble video and audio. Anybody wanting to watch those programs could subscribe to a Service Provider and receive a special “decoder” to unscramble the signal so that he could watch the TV programs. Some pay TV services using MAC already existed because this was a well-designed system where video information was analogue (when the design of MAC had started that was the only practical choice), but all the rest of the information, including audio, was (uncompressed) digital and packet-based! In particular it already contained the necessary infrastructure to provide encryption support.
Pay TV has been a major driver for MPEG-2 use. The content protection systems of analogue pay TV were fully proprietary, but the technology was rather simple and STBs not very costly. The same could have been done with MPEG-2, but the pay TV constituency rightly assessed that there would be benefits in adopting a basic standard infrastructure for the clear-text version of the signal. So MPEG-2 Systems provides two types of messages: Entitlement Control Messages (ECM) and Entitlement Management Messages (EMM) that simplifies implementation of an encrypted broadcasting service.
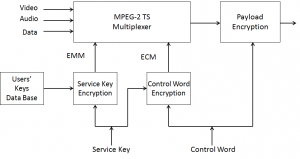
In Figure 1 below the payload is first scrambled with a Control Word (CW). The CW is sent scrambled with a Service Key (SK) via an ECM message. The CW is changed with a frequency of about 1 Hz. The SK is scrambled using a user-specific key and sent via an EMM message. As all users must receive a scrambled SK, this information reaches the intended user within a much longer period of time.
Figure 1 – MPEG-2 content protection (encoder)
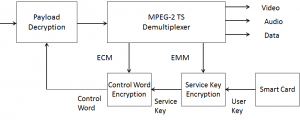
The recovery of the clear-text information is achieved as indicated in Figure 2 where the scrambled SK is extracted from the EMM message and converted to clear text using the User Key (UK) stored in the receiver’s smart card. In its turn this descrambles the CW that can eventually be used to descramble the audio-visual payload. This is where MPEG-2 Systems stops. Nothing is said about the nature of the keys, the scrambling algorithms, etc.
Figure 2 – MPEG-2 content protection (decoder)
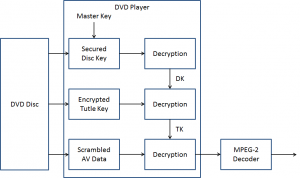
The DVD encryption system – known as Content Scrambling System – is conceptually similar to the system used for pay TV. The player has a Master Key, which is unique to the DVD player manufacturer and accordingly also known as a Player Key (PK). This is equivalent to the key stored in the smart card inserted in a STB. The player decrypts a Disk Key (DK) that is stored in encrypted form on the DVD disc using its PK. Then the player reads the encrypted Title Key (TK) for the file that it has been asked to play. The TK is needed because a DVD usually contains several files, each with its own TK. The TK is decrypted using the DK. Finally, the decrypted TK is used to descramble the actual content.
Figure 3 – Content Protection in DVD
Because of the way encryption support is defined, MPEG-2 provides a standard technology that is universally interoperable when used in clear-text, but encrypted transmission is Service Provider-specific. If I am an End User I have an obvious service requirement: if I am only subscribed to SP A, I should not be able to watch the offer of SP B, unless I decide to subscribe with SP B. In the early digital television days this I had to stack two STBs, but this is not (should not be) a requirement.
This situation was inconvenient to both SP and subscriber. SP needed to find a manufacturer of STBs and make a deal with a security technology provider. The two parties worked together to provide STBs to the SP who then has to purchase the STBs and then subsidise their deployment, the largest cost factor in the SP’s accounts after content itself. The advantage for the SP was the creation of a barrier to the entry of other SPs in the subscriber’s home. The subscriber was inconvenienced because he had to stack as many boxes as there were SPs whose offers he wanted to watch. This was all the more irrational if one thinks that possibly 95% of the electronics in all the boxes is functionally the same. Duplication of STB was needed only because of that security-related 5%.
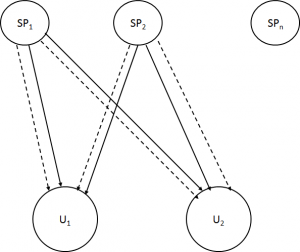
One way to alleviate this problem was to use the same STB to watch different SPs who had an agreement to provide common access to their combined services, as in the figure below
Figure 4 – Simulcrypt (SP1 and SP2)
With “Simulcrypt”, as the system is called, SP1 and SP2 send EMM messages (dotted lines) to the combined set of their subscribers, so that encrypted content (full lines) from both SP1 and SP2 can be viewed by subscribers of both SPs. This requires that the encrypted SK be sent using the UKs of both SPs. The system only works if the two SPs share their subscriber databases, hardly something SPs are willing to do because subscribers are the core asset of their business, unless the SPs are two in name but one in practice.
Some bolder attempts have been made to decouple MPEG-2 decoding from access control.
Figure 5 – The DVB and DAVIC approaches to “more open” content protection
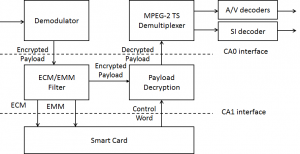
In the figure the CA0 interface, defined by DVB and called Common Interface (CI), is simply an interface where an external, SP-specific, box is plugged: scrambled streams enter the box and leave the box as clear-text. STB’s with CI are expensive and the external device is also expensive because of the high-speed electronics. Further, the clear-text program crosses the SI and can be easily tapped. The CA1 interface, defined by DAVIC, is more elaborate, with low bitrate ECM and EMM signals entering an external device (a smart card) and the control word entering the STB. The DAVIC solution would not suffer from the shortcomings of CI because it only handles the low bitrate EMM and ECM messages and does not provide access to clear-text signals, but requires some form of standardisation that SPs have been loath to accept.
Another solution that has taken root in several countries is to embed all Conditional Access (CA) technologies used in a country for Digital Terrestrial Broadcasting in one set top box. Practical as it may appear, this solution ratifies the existence of a security technology club where it would be hard for a new security company to enter.
Several years ago, European regulators did not perceive the apparent contradiction when they mandated, in one of their directives, the use of MPEG-2 for source coding and multiplexing but remained silent about the Conditional Access (CA) part. Much as I am flattered by the idea that the use of MPEG-2 is made legally binding in Europe if somebody wants to broadcast, I cannot help but wonder about the meaning of such an imposition. If the STB is proprietary because of CA, so could be source coding and multiplexing. Why should there ever have been a directive? On the other hand we see that today the creation of monopolies in information provision is swallowed without a gulp.
I may be the only one, but I am in desperate need for an explanation of what is the meaning and purpose of regulation and competition.